Understanding what is connected to your organization’s networks is no longer optional – it is imperative. Network discovery provides complete visibility of all the endpoints, devices, and systems communicating across business environments.
With exponential growth in network-connected technologies – from mobile devices to IoT sensors – network complexity has skyrocketed. On average, 25 new devices are added to enterprise networks every day. Can you confidently say your IT teams have identified each one?
This guide will explain what network discovery entails, the immense benefits it unlocks for modern businesses, and how to implement continuous discovery across on-prem and cloud networks.
Table of Contents
What is Network Discovery?
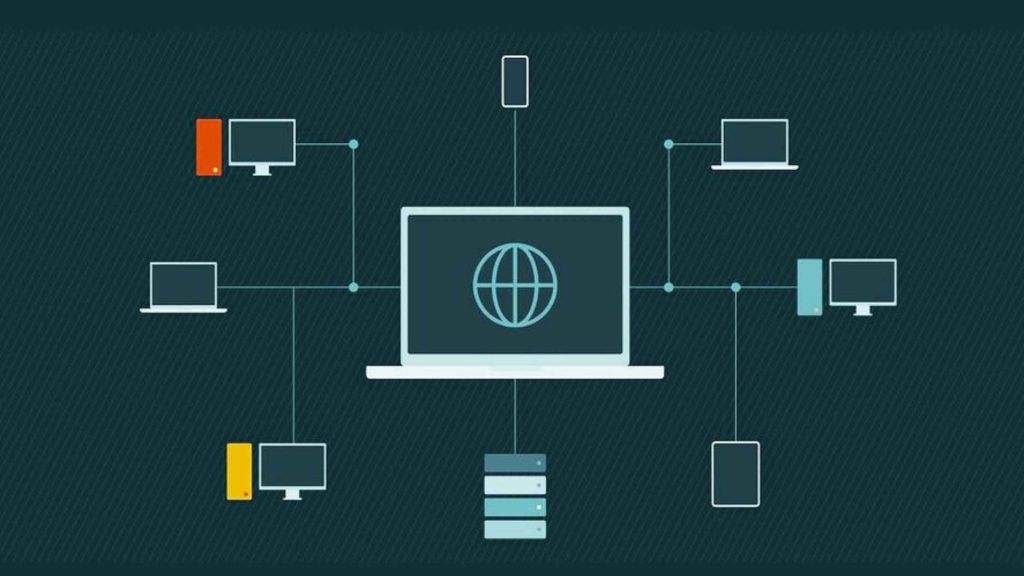
Network discovery refers to the automated process of identifying and inventorying all the active endpoints, servers, systems, devices, and virtual instances connected to an organization’s local area networks (LANs), wide area networks (WANs), wireless networks, and cloud-based networks.
Effective network discovery provides an accurate, up-to-date list of:
- Servers (files, print, database, web, etc.)
- Endpoints (desktops, laptops, tablets, thin clients)
- Mobile devices
- Peripherals (printers, scanners, routers, switches, hubs)
- IoT and OT equipment
- Cloud-based virtual machines and infrastructure
- Unauthorized shadow IT systems
- And more across the extended network environment
Network discovery employs passive traffic analysis, active IP address range scanning, and SNMP device polling to construct a detailed map of all networked assets dispersed across the digital ecosystem.
Why Network Discovery Matters
Comprehensive, continuous network discovery unlocks immense value for modern digitally driven organizations:
Enables Effective Asset Management
By maintaining a live inventory of all hardware and devices on networks, the exact lifecycle status of assets is known. This allows better planning the maintenance, repair and replacement of aging infrastructure and computers based on warranties and leasing terms. Purchase decisions improve.
Provides Foundation for Monitoring
You can’t monitor what you don’t know exists. Discovery exposes all devices using bandwidth and resources. This enables deploying more targeted network performance monitors and efficiency improvements.
Strengthens Security Posture

Uncovering rogue shadow IT systems, outdated equipment missing patches, and unsecured IoT devices enables removing vulnerabilities that attackers exploit. Discovery is a fundamental building block of cyber resilience.
Speeds Troubleshooting
With real-time network topology mapping and device data, IT teams isolate performance issues and outages faster. Quickly pinpointing the source means faster remediation.
Satisfies Compliance Mandates
Standards like PCI DSS, HIPAA, and SOX require meeting strict configuration and device security standards. Discovery audits support compliance reporting.
Optimizes IT Support and Automation
By integrating discovery data with helpdesk systems and scripts, support issues are automatically pre-populated with relevant device data. Workflow efficiency improves.
How Network Discovery Works
There are various techniques network discovery tools employ to identify connected devices:
- Passive traffic analysis silently listens to packets traversing networks to extract details like IP addresses, operating systems, open ports, MAC addresses, and hostnames about transmitters.
- Active scanning sends probes to ranges of IP addresses and ports to elicit responses that reveal active hosts. Useful in cloud environments.
- SNMP polling queries network device operating systems, configurations and system data using Simple Network Management Protocol.
- Integrations with SIEMs, CMDBs, and ITSMs cross-reference asset details from other systems to enhance visibility.
- Machine learning analyzes traffic patterns over time to detect anomalies indicative of new devices. This handles dynamic environments proactively.
Through these methods, network discovery maps out all nodes spanning from endoints to cloud VMs structuring a dynamic topology model.
Maintaining Continuous Discovery
To reap the full benefits, discovery should occur automatically on a scheduled basis, not just periodically. This keeps visibility continuously current as changes occur:
- Scheduled discovery executes on a fixed interval (e.g. daily) to identify new assets and changes.
- Alerts trigger when unexpected devices are detected on networks, signaling rogue devices or misconfigurations.
- Dashboards allow IT administrators to visualize the network topology in real-time and trends over time.
By leveraging discovery tools that employ these capabilities, organizations sustain always-fresh visibility as networks scale and evolve while also improving security.
Top Network Discovery Tools
Leading network discovery platforms include:
- SolarWinds Network Topology Mapper
- ManageEngine OpManager
- Spiceworks Network Mapping
- PRTG Network Monitor
- Vistara IT Automation Platform
Core features range from automated device identification, cloud instance mapping, change tracking and alerts to integration with IT systems management and security workflows.
Conclusion and Next Steps
Complete, up-to-date visibility into the modern tangled technology environment is an imperative few organizations can claim – but one that delivers immense value.
By leveraging network discovery, IT teams remove blindspots across distributed physical, virtual and cloud-based assets. This strengthens IT asset management, monitoring, troubleshooting, security and automation.
Organizations must take three key steps:
- Accept network discovery as a mandatory capability, not an optional extra.
- Select and implement robust automated discovery tools tailored to your environment.
- Integrate and act upon the unprecedented visibility generated.
Network discovery might not be glamorous. But it is foundational. And in the hyperconnected digital age with new threats emerging daily, foundational visibility has become fundamental to managing and securing every aspect of modern network infrastructure holistically.
FAQ’s
For optimal visibility, automated discovery should run on a daily basis. Periodic scanning misses short-lived devices.
Lacking device insights exposes organizations to outages, performance issues, and most importantly, cyberattacks entering through unmonitored shadow IT entry points.
Start by passively scanning production networks, then device-by-device active probing. Integrate findings into CMDBs and monitoring systems. Expand iteratively.
Continuous automated discovery requires tools and dedicated personnel. Larger organizations benefit from professional services assistance for installation and configuration.

