Do you ever wonder how your school’s computers get software updates or performance fixes without the IT team having to visit each one? The answer lies in special software programs called RMM agents. RMM stands for “remote monitoring and management.”
RMM agents, alternatively called little helpers, are installed on each and every device such as computer, laptop or server. Their duty is to monitor the health of a device and notify your managed IT provider of any challenges so that they can be fixed quickly.
This article will clearly explain what exactly RMM agents are, how they work behind the scenes, and why every organization needs them to maintain happy, healthy devices.
Table of Contents
What is an RMM Agent?
An RMM agent is a small software program that manages individual devices remotely. It gets installed onto servers, computers, laptops, smartphones and other endpoints.
You can compare it to the remote control you use for your TV. But instead of changing channels or volume, the RMM agent collects data and allows remote management of each device.
The agent acts as the “eyes and ears” for your managed service provider (MSP) by tracking metrics like:
- Hardware health stats like CPU usage, free disk space, memory etc.
- Software details like list of installed applications, antivirus status, pending updates
- Process activity data like programs running or crashed
- Device usage statistics tracking logins, data usage etc.
It securely passes all this device information back to the RMM platform. This allows your MSP to monitor everything in one unified dashboard.
How Does an RMM Agent Work?
RMM agents work silently in the background after being installed on any endpoint. Here is exactly what happens behind the scenes:
- Quietly collects device data – After installation, the agent runs as a background process. It starts tracking the configured metrics based on what data your MSP wants.
- Encrypted transfer of data – The agent safely sends the collected info at intervals to the RMM vendor’s cloud platform. This uses secure protocols to prevent data leaks.
- Centralized monitoring system – Your MSP gets access to a powerful web-based dashboard to view device reports. Alerts pop up if any issue is detected by agents.
- Enables remote management – Agents facilitate control of devices remotely through features like remote desktop, file transfer, command prompt etc.
- Automates common tasks – Agents can automate things like software patching, antivirus updates etc. across your device fleet.
Here is a diagram summarizing how most RMM agents work:
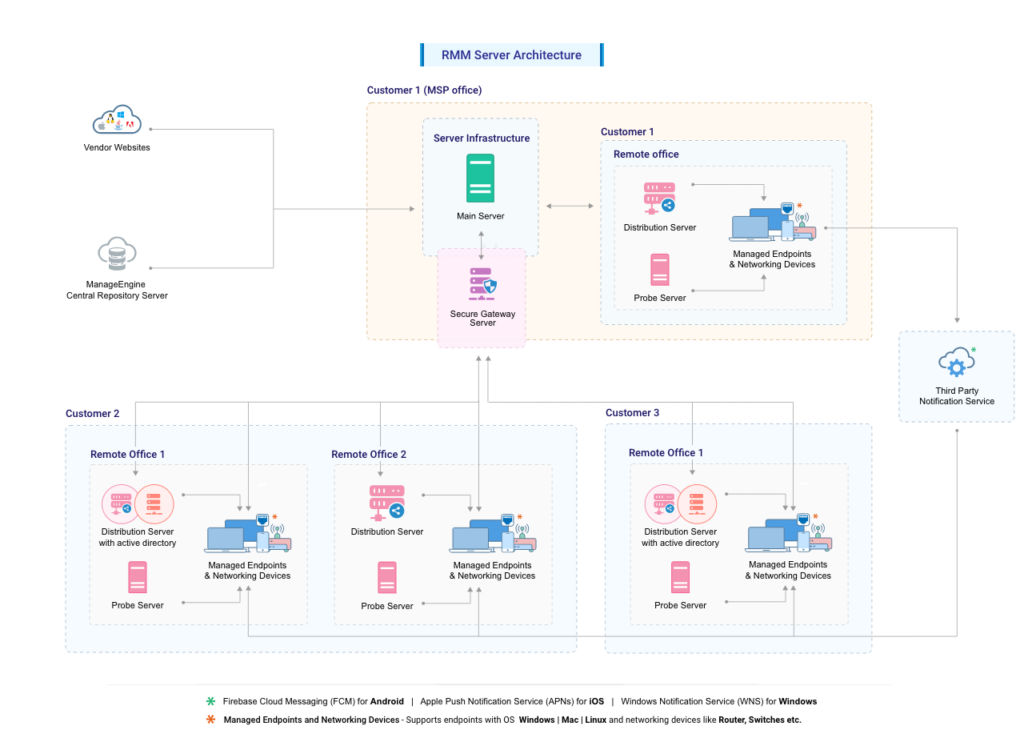
Source: manageengine.com
So in essence, RMM agents act as the conduit for device data to flow to a central monitoring system. This allows smooth remote administration even from different locations.
Why Are RMM Agents Critical for Organizations?
RMM agents serve many invaluable functions from a single pane of glass. Having them installed across your technology infrastructure provides key benefits:
1. Reduce Issues and Downtime
The agent monitors disk space, memory usage, running processes etc. on each device 24/7. If anything is close to a warning threshold, it sends an alert to your MSP’s dashboard.
For example, if a server hard disk is nearing 95% capacity, the agent triggers an early notification. Your IT team can then troubleshoot and prevent disruption before you face a total outage.
2. Support Remote Workforce at Scale
The pandemic saw companies adopt work-from-home models rapidly. For IT teams, supporting a dispersed workforce remotely is difficult.
RMM agents serve as their eyes and ears on each individual device no matter where users are located. This allows effortless centralized management at scale.
3. Simplified IT Management
Monitoring the health status of hundreds of endpoints manually is impossible without RMM automation.
The agents condense reams of granular device data into digestible dashboards and reports. This bird’s eye view makes managing large, complex IT environments very easy.
4. Enhanced Security
Cyberattacks exploit vulnerabilities like missing OS updates or expired antivirus software. RMM agents provide complete visibility into each device’s patch status, open ports etc.
This allows strengthening endpoint security by fixing gaps detected across the fleet via the RMM dashboard.
5. Regulatory Compliance
Industries like healthcare and banking have strict IT compliance rules. RMM tools log device changes like new software installs that auditors verify for protocols like HIPAA.
Their detailed historical logs also help prove compliance by documenting your IT environment’s state at any point in time.
Conclusion
In summary, think of RMM agents as little buddies that keep your endpoints healthy and happy by:
- Telling your MSP how devices are doing
- Alerting them the moment any problem starts
- Enabling quick fixes remotely through the RMM dashboard
Having RMM agents across your technology infrastructure reduces headaches for both end-users and IT teams. They prevent outages, secure devices, simplify management at scale and prove compliance.
Talk to your managed service provider about deploying RMM agents today to reap the time and cost savings. Your devices will thank you!
FAQs
No, RMM agents use very little CPU and memory. Most users don’t even notice it running in the background.
Agents can monitor everything from disk space, network usage to software inventory. But data collection is customizable based on what metrics your MSP wants to track.
Yes, enterprise-grade RMM tools use extremely secure protocols for data transfer and role-based access control for the dashboards. This ensures your device info stays protected.
Admins have granular control over agent permissions. You can limit access to certain files, folders or apps as per your security policies if needed.

