Cyberattacks against small and midsize businesses (SMBs) have exploded in recent years. Lacking the sizable resources larger enterprises dedicate to security, SMBs now present prime targets for everything from ransomware to data theft.
Yet many smaller companies still wonder, “why would hackers bother with us?” or have limited understanding of modern cyber risks. This false sense of safety stems from not yet being impacted directly. However, once breached, the downstream costs and business disruption often prove catastrophic regardless of company size.
This guide examines the most damaging cyber threats now facing SMBs and practical safeguards you must start implementing to protect your company’s livelihood.
Table of Contents
Most Dangerous Threat Vectors Targeting SMBs
Phishing remains the foremost infection vector responsible for approximately 90% of cyber incidents. Deceptive emails with embedded links or attachments convince users to click, unknowingly downloading malware. Attackers research targets across social media then spoof trusted contacts and brands when crafting messages. Links often direct to realistic but fraudulent sites stealing entered credentials.
Ransomware represents another crippling threat whereby hackers infiltrate systems and encrypt critical data. They then extort companies to regain access, threatening permanent loss. Attacks frequently emerge from earlier phishing breaches granting network access. The average ransom sought now exceeds $200,000. Many victims lacking backups fold altogether, while those paying ransoms still average 65 days productivity destroyed.
POS/Payment Card Skimmers inserted into retail payment systems stealthily steal thousands of customer credit card numbers later sold on dark web marketplaces. Equally destructive physical skimmers attached inside pumps at gas stations demonstrate similar objectives.
Insider Threats originate from employees or third parties misusing accessed proprietary data, whether intentionally malicious or via reckless handling. Finance staff or customer service teams often view extensive customer records presenting monetization opportunities.
Third Party Vendor Risks emerge from interconnected systems enabling financial transactions, storing healthcare data, powering online stores, and more. If any external vendor lacks appropriate access controls or security posture, their vulnerabilities become your own.
Cybersecurity Best Practices Critical for SMB Survival
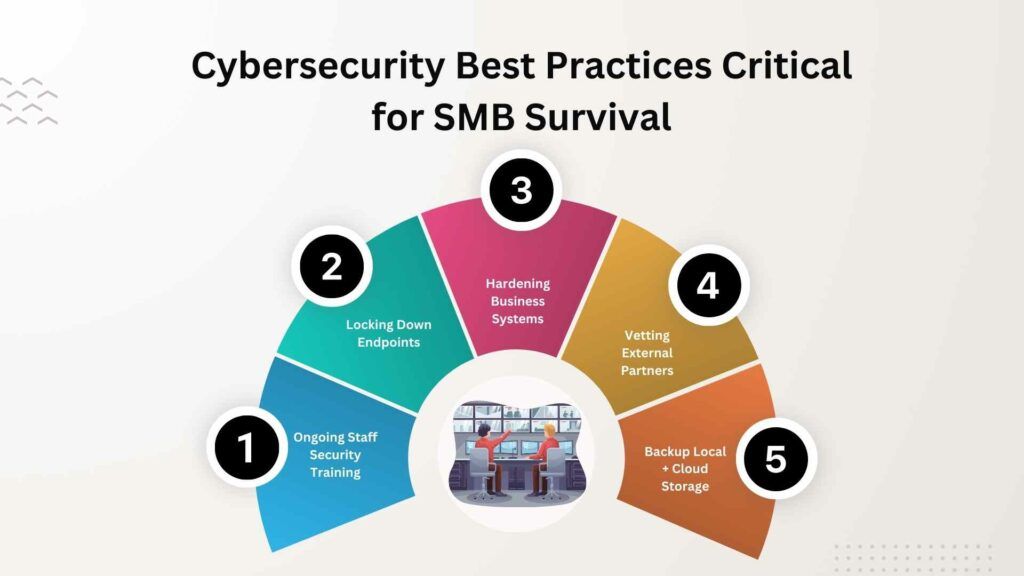
While digital threats seem daunting, taking essential precautions makes a tremendous difference.
Ongoing Staff Security Training
Annual cybersecurity awareness training, simulated phishing tests, and periodic reminder communications teach personnel how to identify and immediately report potential threats. Users represent your last line of defense. Reward vigilance.
Locking Down Endpoints
Every device directly accessing company data should run current antivirus software, receive prompt operating system and browser patch updates that fix known vulnerabilities, and only have approved programs installed. Administrative privileges granting ability to modify system configurations must be strictly limited to IT staff.
For remote workers, mandate VPN connections to restrict network access to company-approved channels only.
Hardening Business Systems
Your central file servers, databases, email platforms and business productivity software also warrant priority attention:
- Harden access with multi-factor authentication requirements for admins
- Maintain up-to-date patched versions without running outdated software
- Review user roles and permission assignments quarterly
- Install endpoint detection and response (EDR) tools continuously monitoring for internal behavioral anomalies
- Centralize activity log collection with automation to surface red flags
Vetting External Partners
Closely evaluate the access controls and security measures for any vendor touching financial data, healthcare records, ecommerce platform integrations or other sensitive systems.
Require disclosure of past security incidents and alignment with industry standards. Limit data access only to essential needs. Bind partners contractually to maintain specific controls and notify your company regarding suspected incidents.
Backup Local + Cloud Storage
Secure, encrypted backups across all business systems facilitate recovery should worst-case ransomware or hardware failures hit. Test restoration processes regularly with access to secured backup data sources completely isolated from corporate servers which could become compromised.
Recognizing and Responding to Security Incidents
While preventative measures aim to avoid incidents outright, remaining vigilant for subtle red flag indicators represents another critical defense layer.
Warning signs range from staff receiving odd requests for sensitive data, unapproved system modifications, antivirus alerts, suspicious login locations, through overt website defacements or data encryption locking access.
If a cyberattack penetrates defenses, time becomes critical:
- Immediately pull affected systems offline to contain spread
- Seek incident response help stating exactly what you observed but don’t yet know underlying cause
- Don’t pay any ransoms since encrypted files may be unrecoverable anyway and payments spur more criminal attacks
- Backup restoration represents the best path to data recovery without playing ransom gamble
Saving malware samples, suspicious messages, activity logs and configurations aids forensic investigators assessing root causes and required remediation. Prompt yet careful containment responses allow the best chance to limit damages.
FAQs
Depending on company size and existing technology investments, basic awareness training, managed antivirus services, VPNs, backups and monitoring range from $5-20 monthly per employee. Upgrading aging IT infrastructure carries larger capital costs but prevents much more expensive incidents.
Vigilant employees represent your absolute best defense given users directly interact with attack vectors. Prioritizing interactive cybersecurity education so your team proactively spots and avoids common social engineering lures attackers rely on to gain initial access is by far most effective. Technology alone cannot save the day.
Without prompt containment isolating infections plus recent restorable backups, businesses losing access to critical systems or data wrestle with weeks if not months-long outages. Some unfortunately never reopen following major incidents underscoring the importance of planning for worst case scenarios.
Reputable managed service providers offer detailed compromise assessments identifying vulnerabilities in usage policies, software configurations and user practices. Ongoing monitoring and training services tailored to SMB budgets also enhance readiness continuously.

